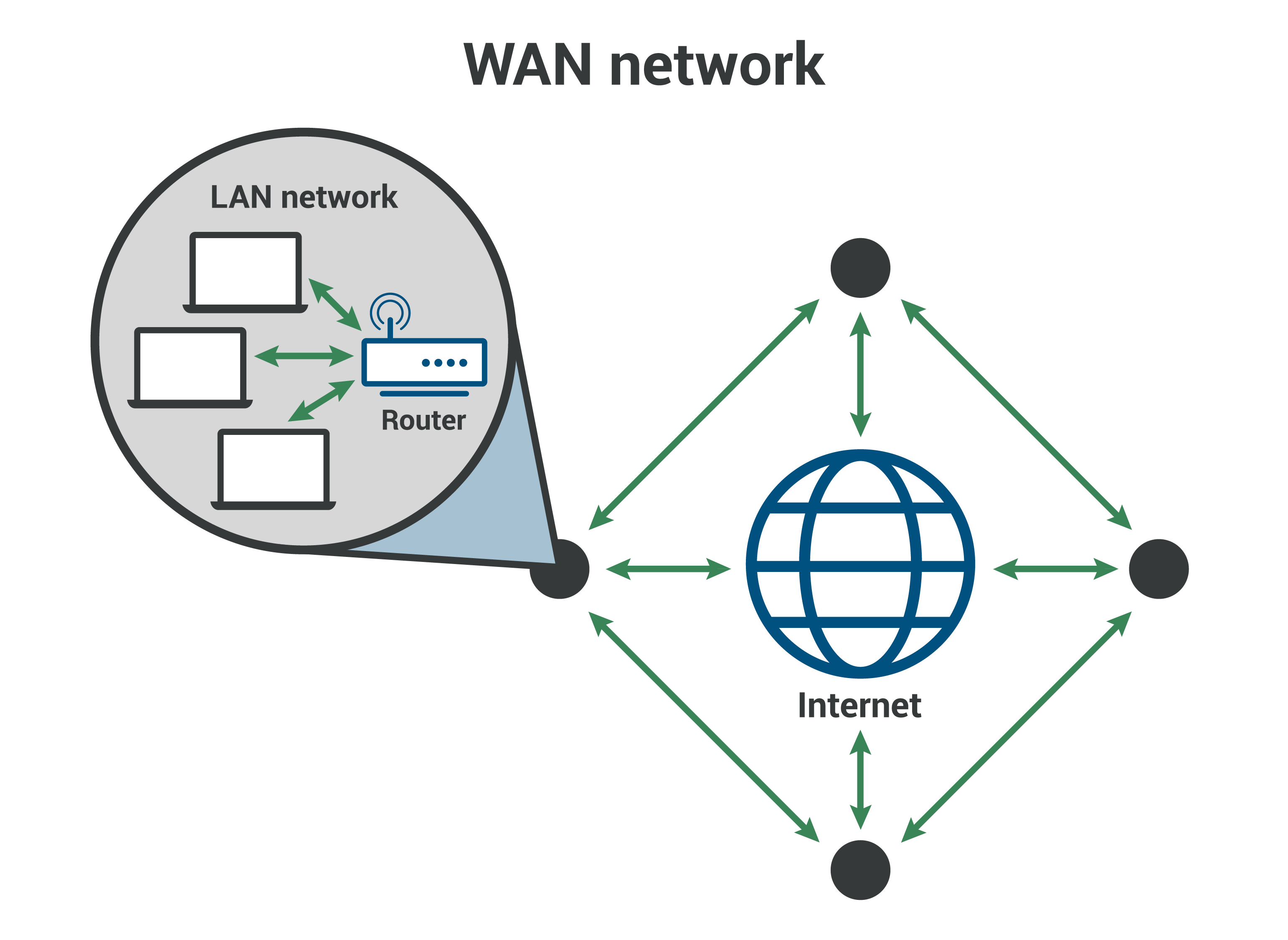
WAN blocking, also known as wide area network blocking, is a network security measure that prevents unauthorized access to a private network from the public internet. It is implemented by using a firewall or router to block traffic from specific IP addresses or ranges of IP addresses.
WAN blocking is an important security measure for businesses and organizations of all sizes. It can help to protect sensitive data from being accessed by unauthorized users, and it can also help to prevent the spread of malware and other cyber threats. WAN blocking can also be used to improve network performance by reducing the amount of unwanted traffic on the network.
There are a number of different ways to implement WAN blocking. One common method is to use a firewall to block traffic from specific IP addresses or ranges of IP addresses. Another method is to use a router to block traffic from specific ports or protocols.
WAN blocking is an effective way to improve network security and performance. It is a relatively simple and inexpensive measure that can be implemented by businesses and organizations of all sizes.
WAN Blocking
WAN blocking is a critical network security measure that helps protect private networks from unauthorized access. It involves blocking traffic from specific IP addresses or ranges of IP addresses using firewalls or routers.
- Security: WAN blocking prevents unauthorized access to sensitive data and resources.
- Malware Protection: It helps prevent the spread of malware and other cyber threats.
- Network Performance: WAN blocking reduces unwanted traffic, improving network performance.
- Compliance: It supports compliance with regulations and industry standards.
- Cost-Effective: WAN blocking is a relatively inexpensive security measure.
- Scalable: It can be implemented in networks of all sizes.
- Flexible: WAN blocking can be customized to meet specific security requirements.
- Easy to Implement: It can be easily implemented using firewalls or routers.
In summary, WAN blocking plays a vital role in network security by preventing unauthorized access, protecting against cyber threats, improving network performance, and supporting compliance. It is a cost-effective, scalable, flexible, and easy-to-implement solution that is essential for businesses and organizations of all sizes.
Security
WAN blocking is a critical security measure that helps protect private networks from unauthorized access to sensitive data and resources. It involves blocking traffic from specific IP addresses or ranges of IP addresses using firewalls or routers.
- Protection of Confidential Data: WAN blocking prevents unauthorized users from accessing confidential data, such as financial records, customer information, and trade secrets. This is especially important for businesses and organizations that handle sensitive data.
- Prevention of Data Breaches: WAN blocking helps prevent data breaches by blocking unauthorized access to network resources. This can help protect organizations from financial losses, reputational damage, and legal liabilities.
- Compliance with Regulations: WAN blocking can help organizations comply with regulations and industry standards that require the protection of sensitive data. For example, the Health Insurance Portability and Accountability Act (HIPAA) requires healthcare organizations to protect the privacy of patient data.
In summary, WAN blocking is an essential security measure that helps protect sensitive data and resources from unauthorized access. It is a cost-effective and easy-to-implement solution that can help organizations comply with regulations and protect their reputation.
Malware Protection
WAN blocking plays a crucial role in malware protection by preventing the spread of malware and other cyber threats. Malware, such as viruses, worms, and ransomware, can infect computers and networks, causing data loss, financial damage, and operational disruptions.
WAN blocking helps prevent malware infections by blocking traffic from known malicious IP addresses and websites. It also blocks access to malicious files and executable code, preventing them from being downloaded and executed on the network.
For example, if a known malicious IP address is identified as the source of a malware attack, WAN blocking can be used to block all traffic from that IP address, preventing the malware from spreading to other computers on the network.
WAN blocking is an essential component of a comprehensive malware protection strategy. It works in conjunction with other security measures, such as antivirus software and firewalls, to provide multiple layers of protection against malware and other cyber threats.
Network Performance
WAN blocking plays a crucial role in improving network performance by reducing unwanted traffic. Unwanted traffic, such as spam, malicious traffic, and unnecessary updates, can consume significant network bandwidth and resources, slowing down network speeds and affecting overall performance.
By blocking unwanted traffic, WAN blocking helps to free up network bandwidth and resources, allowing legitimate traffic to flow more efficiently. This results in faster network speeds, reduced latency, and improved application performance.
For example, in a corporate network, WAN blocking can be used to block access to known spam and malware websites. By doing so, it prevents these malicious websites from consuming network bandwidth and potentially infecting computers on the network.
WAN blocking can also be used to improve network performance in remote areas with limited bandwidth. By blocking unnecessary updates and other non-essential traffic, WAN blocking can help to ensure that critical applications have the bandwidth they need to perform optimally.
In summary, WAN blocking is an effective way to improve network performance by reducing unwanted traffic. It is a cost-effective and easy-to-implement solution that can benefit businesses and organizations of all sizes.
Compliance
WAN blocking plays a vital role in supporting compliance with regulations and industry standards. Many regulations and standards require organizations to implement security measures to protect sensitive data and prevent unauthorized access to their networks. WAN blocking is a key security measure that helps organizations meet these compliance requirements.
For example, the Health Insurance Portability and Accountability Act (HIPAA) requires healthcare organizations to protect the privacy and security of patient health information. WAN blocking can be used to block unauthorized access to patient data from external networks, helping healthcare organizations comply with HIPAA regulations.
Another example is the Payment Card Industry Data Security Standard (PCI DSS), which requires businesses that process credit card payments to implement security measures to protect cardholder data. WAN blocking can be used to block unauthorized access to payment card data from external networks, helping businesses comply with PCI DSS requirements.
WAN blocking is a cost-effective and easy-to-implement solution that can help organizations comply with a wide range of regulations and industry standards. It is an essential component of a comprehensive security strategy for any organization that handles sensitive data.
Cost-Effective
WAN blocking is a cost-effective security measure because it does not require significant investment in hardware or software. It can be implemented using existing firewalls or routers, and it does not require specialized expertise to configure and maintain. This makes it an attractive option for businesses and organizations of all sizes, including those with limited budgets.
- Low Hardware and Software Costs: WAN blocking can be implemented using existing network infrastructure, eliminating the need for additional hardware or software purchases.
- Reduced IT Expenses: WAN blocking does not require specialized expertise to configure and maintain, reducing the need for costly IT support and consulting services.
- Improved ROI: WAN blocking provides a high return on investment by protecting sensitive data and preventing cyber threats, which can lead to significant cost savings in the long run.
- Scalability and Flexibility: WAN blocking can be easily scaled to meet the changing needs of organizations, making it a cost-effective solution for both small and large networks.
In summary, WAN blocking is a cost-effective security measure that provides a high return on investment. It is easy to implement and maintain, and it can be scaled to meet the needs of organizations of all sizes. By protecting sensitive data and preventing cyber threats, WAN blocking helps organizations save money and mitigate risks.
Scalable
The scalability of WAN blocking makes it a valuable security measure for organizations of all sizes. Unlike some security solutions that may be limited to specific network sizes or configurations, WAN blocking can be easily adapted to meet the needs of small, medium, and large networks. This scalability is particularly important in today's dynamic business environment, where organizations are constantly evolving and expanding their networks.
For example, a small business with a limited number of employees and devices can implement WAN blocking using a simple firewall or router. As the business grows and adds more employees and devices, the WAN blocking solution can be easily scaled to accommodate the increased network size and traffic. This scalability ensures that the organization's network remains protected from unauthorized access and cyber threats.
In larger organizations with complex networks, WAN blocking can be implemented using more sophisticated security appliances or virtualized solutions. These solutions provide greater scalability and flexibility, allowing organizations to customize WAN blocking policies based on specific network segments, user groups, or applications. By leveraging scalable WAN blocking solutions, organizations can effectively protect their networks from unauthorized access, regardless of their size or complexity.
In summary, the scalability of WAN blocking is a critical factor that contributes to its effectiveness and widespread adoption. By providing a flexible and adaptable security solution that can be tailored to networks of all sizes, WAN blocking empowers organizations to protect their sensitive data and resources from unauthorized access and cyber threats.
Flexible
The flexibility of WAN blocking is a critical aspect that enhances its effectiveness and adaptability in meeting diverse security requirements. WAN blocking can be customized to suit the specific security needs of an organization, allowing for tailored protection strategies based on unique network configurations, data sensitivity levels, and regulatory compliance mandates.
For instance, organizations operating in highly regulated industries, such as healthcare or finance, can leverage WAN blocking to comply with industry-specific regulations and standards. By customizing WAN blocking rules to restrict access to sensitive data and resources, organizations can meet compliance requirements and mitigate risks associated with unauthorized access and data breaches.
Furthermore, WAN blocking provides flexibility in defining granular access controls. Network administrators can configure WAN blocking policies to allow or deny access based on specific IP addresses, ports, protocols, or even specific applications. This granular control enables organizations to implement context-aware security measures, ensuring that only authorized users and devices have access to critical resources while restricting access to potential threats.
In summary, the flexibility of WAN blocking empowers organizations to tailor their security strategies to meet specific requirements, ensuring comprehensive protection against unauthorized access and cyber threats. By providing granular control and adaptability, WAN blocking plays a crucial role in safeguarding sensitive data, maintaining compliance, and ensuring the overall security posture of an organization's network.
Easy to Implement
The ease of implementing WAN blocking is a significant advantage that contributes to its widespread adoption. WAN blocking can be easily deployed using existing network infrastructure, leveraging firewalls or routers that are commonly found in most organizations. This straightforward implementation process reduces the complexity and cost associated with deploying security measures, making WAN blocking accessible to organizations of all sizes and technical capabilities.
For instance, a small business with limited IT resources can quickly implement WAN blocking using their existing firewall. By configuring the firewall to block traffic from unauthorized IP addresses or ports, the business can effectively protect its network from external threats without the need for complex or expensive security solutions.
Similarly, large enterprises with sophisticated network architectures can leverage their existing routers to implement WAN blocking. By incorporating WAN blocking rules into their routing tables, enterprises can control and restrict traffic flow across their networks, ensuring that only authorized traffic is allowed.
In summary, the ease of implementing WAN blocking using firewalls or routers makes it a practical and cost-effective security measure. This simplicity enables organizations to quickly and effectively protect their networks from unauthorized access and cyber threats, regardless of their size or technical expertise.
WAN Blocking FAQs
This section addresses frequently asked questions (FAQs) about WAN blocking, providing clear and informative answers to common concerns and misconceptions.
Question 1: What is WAN blocking?
WAN blocking is a network security measure that involves blocking unauthorized access to a private network from the public internet. It is implemented using firewalls or routers to restrict traffic from specific IP addresses or ranges of IP addresses.
Question 2: Why is WAN blocking important?
WAN blocking is crucial for protecting sensitive data, preventing the spread of malware, improving network performance, and ensuring compliance with regulations and industry standards.
Question 3: How does WAN blocking work?
WAN blocking works by using firewalls or routers to block traffic from specific IP addresses or ranges of IP addresses. This prevents unauthorized users from accessing the private network and its resources.
Question 4: What are the benefits of WAN blocking?
WAN blocking offers numerous benefits, including improved security, reduced risk of malware infections, enhanced network performance, and support for compliance with regulations and industry standards.
Question 5: What are the limitations of WAN blocking?
WAN blocking may introduce some limitations, such as the potential for false positives (blocking legitimate traffic) and the need for careful configuration to avoid unintended consequences.
Question 6: What are some best practices for implementing WAN blocking?
Best practices for implementing WAN blocking include defining clear security policies, using reputable firewalls or routers, regularly updating security rules, and monitoring network traffic for suspicious activity.
In summary, WAN blocking is a vital network security measure that provides numerous benefits for organizations of all sizes. By understanding the importance, functionality, and best practices of WAN blocking, organizations can effectively protect their networks from unauthorized access and cyber threats.
Transition to the next article section: Exploring Advanced WAN Blocking Techniques
WAN Blocking Best Practices
WAN blocking is a critical security measure for protecting networks from unauthorized access and cyber threats. To effectively implement and manage WAN blocking, consider the following best practices:
Tip 1: Define Clear Security Policies
Establish comprehensive security policies that outline the rules and criteria for WAN blocking. Clearly define which IP addresses, ports, and protocols should be blocked to prevent unauthorized access and protect sensitive data.
Tip 2: Use Reputable Firewalls or Routers
Select and deploy reputable and reliable firewalls or routers that provide robust WAN blocking capabilities. Ensure that these devices are properly configured and maintained to effectively enforce security policies.
Tip 3: Regularly Update Security Rules
Regularly review and update WAN blocking rules to address new threats and vulnerabilities. Stay informed about emerging cyber threats and update security rules promptly to prevent exploitation.
Tip 4: Monitor Network Traffic for Suspicious Activity
Continuously monitor network traffic for suspicious activity that may indicate attempted unauthorized access or malicious behavior. Use intrusion detection systems or other monitoring tools to identify and respond to potential threats.
Tip 5: Implement Multi-Layered Security
Combine WAN blocking with other security measures, such as firewalls, intrusion prevention systems, and antivirus software, to create a multi-layered defense against cyber threats. This comprehensive approach enhances overall network security and reduces the risk of successful attacks.
Tip 6: Educate Users About Security Risks
Educate users about the importance of cybersecurity and the role of WAN blocking in protecting the network. Encourage responsible behavior, such as avoiding suspicious websites and using strong passwords, to minimize the risk of security breaches.
Tip 7: Test and Validate WAN Blocking Configuration
Regularly test and validate the configuration of WAN blocking to ensure it is working as intended. Conduct penetration testing or use other methods to assess the effectiveness of the blocking rules and identify any potential weaknesses.
Tip 8: Seek Professional Assistance When Needed
If necessary, seek professional assistance from cybersecurity experts to design, implement, and manage WAN blocking effectively. They can provide guidance, technical support, and ongoing monitoring to ensure optimal network security.
In conclusion, by following these best practices, organizations can strengthen their WAN blocking strategies, protect their networks from unauthorized access and cyber threats, and maintain a secure and resilient IT infrastructure.
WAN Blocking
WAN blocking has emerged as a cornerstone of modern network security strategies. By effectively restricting unauthorized access and mitigating cyber threats, WAN blocking safeguards sensitive data, enhances network performance, and supports compliance with industry standards. This article has explored the significance, functionality, benefits, and best practices of WAN blocking, providing valuable insights for organizations seeking to protect their networks from evolving cyber threats.
In today's digital landscape, WAN blocking is not merely an option but a necessity for organizations prioritizing the security and integrity of their networks. Its ability to prevent unauthorized access, thwart malware attacks, and improve network efficiency makes it an indispensable tool for safeguarding valuable data and maintaining business continuity. By embracing WAN blocking and adhering to its best practices, organizations can proactively secure their networks, protect sensitive information, and stay ahead of the ever-changing cybersecurity landscape.

Detail Author:
- Name : Dr. Braulio Emard III
- Username : jensen86
- Email : noel.mcglynn@roob.org
- Birthdate : 1976-11-07
- Address : 299 Ullrich Stravenue Port Lucienne, TN 74083
- Phone : 831-658-8440
- Company : Schmitt LLC
- Job : Gaming Service Worker
- Bio : Voluptate fuga ratione labore dolores facere. Deserunt quo repudiandae quam similique porro veniam. In cupiditate earum tenetur dicta.
Socials
facebook:
- url : https://facebook.com/jordy_bode
- username : jordy_bode
- bio : Aut esse aut sunt iure impedit. Officiis et aliquid omnis inventore alias.
- followers : 447
- following : 2635
tiktok:
- url : https://tiktok.com/@bode1971
- username : bode1971
- bio : Eaque recusandae quibusdam quis.
- followers : 5869
- following : 1548
instagram:
- url : https://instagram.com/bode2006
- username : bode2006
- bio : Quisquam suscipit architecto earum rerum eos. Blanditiis eum eos eum.
- followers : 6979
- following : 2650
linkedin:
- url : https://linkedin.com/in/jbode
- username : jbode
- bio : Quos maxime id odit voluptatibus amet est ut.
- followers : 3842
- following : 1739
twitter:
- url : https://twitter.com/jbode
- username : jbode
- bio : Fugit sint quidem laborum nam. Quo ut ab nulla. Modi voluptas delectus aut consequuntur impedit. Quasi vel ut assumenda sed.
- followers : 6650
- following : 1433