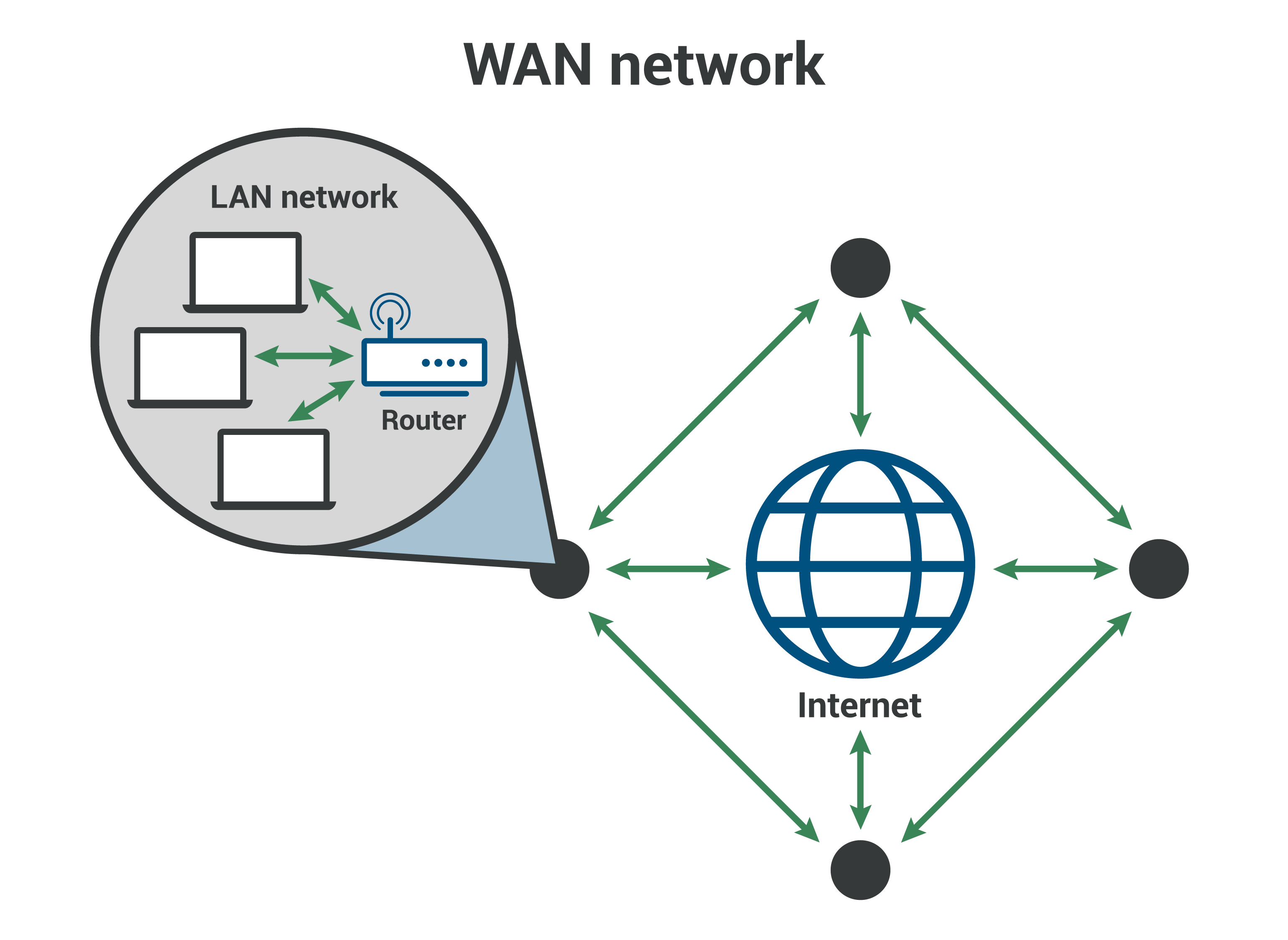
WAN blocking is a security measure that prevents unauthorized access to a Wide Area Network (WAN) from the Internet. It is implemented by using a firewall or router to block incoming traffic from the Internet on specific ports or IP addresses.
WAN blocking is important because it helps to protect from cyberattacks, such as malware and phishing attacks. It can also help to improve network performance by reducing the amount of unwanted traffic on the network.
WAN blocking has been around for many years, but it has become increasingly important in recent years as the number of cyberattacks has increased. Today, WAN blocking is considered to be an essential security measure for any business that has a WAN.
What is WAN Blocking
WAN blocking is a critical security measure that helps protect Wide Area Networks (WANs) from unauthorized access and cyberattacks. Here are ten key aspects of WAN blocking:
- Definition: Blocking unauthorized access to a WAN from the Internet.
- Purpose: Protects against cyberattacks, improves network performance.
- Implementation: Firewalls or routers block traffic on specific ports/IP addresses.
- Importance: Essential security measure for businesses with WANs.
- Benefits: Protection from malware, phishing, and other threats.
- Historical Context: Has been around for many years, becoming increasingly important with the rise of cyberattacks.
- Technical Considerations: Requires careful configuration and maintenance.
- Related Technologies: Firewalls, intrusion detection systems, access control lists.
- Best Practices: Regular updates, monitoring, and testing.
- Future Trends: Integration with cloud-based security solutions.
In summary, WAN blocking is a crucial security measure that helps protect WANs from a wide range of threats. By understanding the key aspects outlined above, organizations can effectively implement and maintain WAN blocking solutions to enhance their network security posture.
Definition
This definition captures the essence of WAN blocking, succinctly describing its primary purpose: to prevent unauthorized entities from gaining access to a Wide Area Network (WAN) via the Internet. WAN blocking is a critical component of network security, as it acts as a barrier against malicious actors seeking to exploit vulnerabilities or launch cyberattacks.
The significance of this definition lies in its ability to convey the fundamental concept of WAN blocking. It establishes a clear understanding of the problem that WAN blocking addresses, namely the threat of unauthorized access from the Internet. This understanding is crucial for organizations to recognize the importance of implementing WAN blocking measures to protect their networks and data from potential security breaches.
In practice, WAN blocking is implemented using firewalls or routers to block incoming traffic from the Internet on specific ports or IP addresses. This helps prevent unauthorized access attempts, such as malware infections, phishing attacks, and data breaches. By understanding the definition and purpose of WAN blocking, organizations can effectively deploy and manage these security measures to enhance their network security posture.
Purpose
WAN blocking serves a dual purpose: protecting against cyberattacks and improving network performance. By blocking unauthorized access to a WAN from the Internet, WAN blocking helps prevent a wide range of cyber threats, such as malware infections, phishing attacks, and data breaches.
- Protection against cyberattacks: WAN blocking acts as a barrier against malicious actors seeking to exploit vulnerabilities or launch cyberattacks on a WAN. By preventing unauthorized access from the Internet, WAN blocking helps reduce the risk of security breaches and data loss.
- Improved network performance: WAN blocking can also improve network performance by reducing the amount of unwanted traffic on the network. By blocking unnecessary or malicious traffic, WAN blocking helps ensure that critical business applications and data have the necessary bandwidth and resources to operate efficiently.
In summary, the purpose of WAN blocking is to protect against cyberattacks and improve network performance. By understanding this dual purpose, organizations can effectively implement and manage WAN blocking solutions to enhance their network security posture and overall network efficiency.
Implementation
In the context of WAN blocking, the implementation involves using firewalls or routers to block incoming traffic from the Internet on specific ports or IP addresses. This plays a critical role in preventing unauthorized access to a WAN and safeguarding it from cyber threats.
- Firewall Configuration: Firewalls are network security devices that monitor and control incoming and outgoing network traffic based on predefined rules. In WAN blocking, firewalls can be configured to block traffic from specific ports or IP addresses associated with known threats or unauthorized access attempts.
- Router Configuration: Routers are networking devices that forward data packets between different networks. WAN blocking can be implemented on routers by configuring access control lists (ACLs) to block traffic from specific ports or IP addresses at the network edge.
- Port Blocking: Ports are logical endpoints that applications use to communicate over a network. By blocking specific ports, such as those commonly used by malicious software or unauthorized access tools, WAN blocking prevents these threats from establishing connections and compromising the network.
- IP Address Blocking: IP addresses are unique identifiers assigned to devices on a network. WAN blocking can be implemented by blocking traffic from specific IP addresses or ranges of IP addresses associated with known malicious actors or suspicious activities.
By understanding the implementation details of WAN blocking, organizations can effectively configure and manage these security measures to protect their WANs from a wide range of cyber threats. WAN blocking plays a crucial role in maintaining network security and ensuring the integrity and confidentiality of data.
Importance
In the context of "what is WAN blocking", its importance stems from the critical role it plays in safeguarding Wide Area Networks (WANs) used by businesses. WAN blocking is an essential security measure for businesses that rely on WANs for various purposes, including connecting multiple locations, accessing cloud services, and facilitating remote work.
- Protection from Cyber Threats: WAN blocking protects WANs from a range of cyber threats, such as malware, phishing attacks, and unauthorized access attempts. By blocking malicious traffic from the Internet, WAN blocking helps prevent data breaches, system compromise, and financial losses.
- Compliance with Regulations: Many industries and regulations require businesses to implement appropriate security measures to protect sensitive data and comply with privacy laws. WAN blocking is a key component of a comprehensive security strategy, helping businesses meet compliance requirements and avoid potential legal liabilities.
- Ensuring Business Continuity: WANs are essential for business operations, connecting employees, customers, and partners. WAN blocking helps ensure business continuity by preventing cyberattacks that could disrupt network connectivity, data access, and critical business processes.
- Improved Network Performance: WAN blocking can also improve network performance by reducing the amount of unwanted traffic on the network. By blocking malicious traffic and unnecessary connections, WAN blocking frees up bandwidth and resources for legitimate business activities.
In summary, WAN blocking is an essential security measure for businesses with WANs, providing protection from cyber threats, ensuring compliance, safeguarding business continuity, and improving network performance. Understanding the importance of WAN blocking is crucial for businesses to make informed decisions about their network security strategies.
Benefits
WAN blocking provides numerous benefits, including protection from a range of cyber threats that can compromise the security and integrity of a Wide Area Network (WAN). Malware, phishing, and other threats pose significant risks to businesses and organizations, and WAN blocking plays a critical role in mitigating these risks.
- Protection from Malware: Malware encompasses a wide range of malicious software, including viruses, worms, and Trojans. WAN blocking helps protect WANs from malware infections by blocking traffic from known malicious IP addresses or ports associated with malware distribution. By preventing malware from entering the network, WAN blocking safeguards critical systems and data from damage or theft.
- Defense against Phishing Attacks: Phishing is a type of cyberattack that attempts to trick users into revealing sensitive information, such as passwords or financial data, by imitating legitimate websites or emails. WAN blocking can help defend against phishing attacks by blocking access to known phishing websites or by inspecting incoming emails for suspicious content and attachments.
- Mitigation of Other Threats: In addition to malware and phishing, WAN blocking can also mitigate other threats, such as spam, denial-of-service attacks, and unauthorized access attempts. By blocking unsolicited or malicious traffic, WAN blocking helps reduce the overall threat landscape and protects WANs from a wide range of cyber threats.
In summary, the benefits of WAN blocking include protection from malware, phishing, and other threats, thereby safeguarding the security and integrity of WANs. Understanding these benefits is crucial for organizations to recognize the value of WAN blocking as a critical security measure and to implement it effectively to protect their networks and data.
Historical Context
The historical context of WAN blocking is closely intertwined with the evolution of cyber threats and the increasing reliance on WANs for business operations. WAN blocking has been around for many years, but its importance has grown exponentially with the rise of sophisticated cyberattacks.
- Emergence of Cyber Threats: In the early days of networking, WANs were primarily used for connecting remote offices and data centers. However, as the Internet became more prevalent, so did the threats to network security. Cybercriminals developed various techniques to exploit vulnerabilities in networks and systems, leading to the emergence of malware, phishing attacks, and other threats.
- Increased WAN Adoption: Over the years, WANs have become increasingly critical for businesses of all sizes. With the rise of cloud computing, remote work, and global supply chains, WANs are essential for connecting employees, partners, and customers across dispersed locations. This increased adoption has made WANs a more attractive target for cyberattacks.
- Evolving Threat Landscape: The cyber threat landscape is constantly evolving, with new and more sophisticated attacks emerging regularly. Cybercriminals are continually finding new ways to exploit vulnerabilities in networks and systems, making it essential for organizations to implement robust security measures, including WAN blocking, to protect their networks and data.
- Regulatory Compliance: In recent years, there has been a growing emphasis on data protection and privacy regulations. Many industries and countries have implemented laws and regulations that require organizations to implement appropriate security measures to protect personal data and comply with data protection standards. WAN blocking is a key component of a comprehensive security strategy, helping organizations meet compliance requirements and avoid potential legal liabilities.
In summary, the historical context of WAN blocking highlights its evolution over time in response to the rise of cyberattacks and the increasing reliance on WANs. Understanding this historical context is crucial for organizations to appreciate the importance of WAN blocking as a critical security measure in today's digital landscape.
Technical Considerations
Technical considerations play a crucial role in the implementation and effectiveness of WAN blocking. Careful configuration and maintenance are essential to ensure that WAN blocking is properly deployed and as intended.
- Firewall and Router Configuration
WAN blocking is typically implemented using firewalls or routers. These devices must be carefully configured to block traffic from specific ports or IP addresses associated with known threats or unauthorized access attempts. Misconfigurations can lead to security gaps or unintended blocking of legitimate traffic.
- Regular Updates and Patching
Cybercriminals are constantly developing new techniques to exploit vulnerabilities in firewalls and routers. It is essential to regularly update and patch these devices with the latest security fixes to address known vulnerabilities and prevent potential attacks.
- Monitoring and Logging
Continuously monitoring and logging WAN blocking activities is crucial for detecting and responding to potential security incidents. Logs should be analyzed regularly to identify any suspicious activity or attempts to bypass WAN blocking measures.
- Testing and Validation
Regular testing and validation of WAN blocking configurations are essential to ensure their effectiveness and identify any weaknesses. Penetration testing or vulnerability assessments can be conducted to simulate real-world attacks and validate the robustness of WAN blocking measures.
By carefully considering these technical aspects and implementing them effectively, organizations can enhance the security of their WANs and mitigate the risks associated with cyber threats.
Related Technologies
In the context of WAN blocking, related technologies such as firewalls, intrusion detection systems (IDS), and access control lists (ACLs) play critical roles in enhancing network security and complementing WAN blocking measures.
Firewalls act as the first line of defense by blocking unauthorized access to a WAN from the Internet. They examine incoming and outgoing network traffic based on predefined rules and filter out malicious or unwanted traffic. IDS monitors network traffic for suspicious activities and generates alerts when potential threats are detected, providing real-time protection against sophisticated attacks.
ACLs are sets of rules that define which network traffic is allowed or denied based on specific criteria, such as source and destination IP addresses, ports, or protocols. They are often implemented on routers or firewalls to control access to specific network resources or segments, further strengthening the overall security posture.
The integration of these related technologies with WAN blocking provides a comprehensive approach to network security. By combining the capabilities of firewalls, IDS, and ACLs, organizations can effectively protect their WANs from a wide range of cyber threats, including malware, phishing attacks, unauthorized access attempts, and data breaches.
Understanding the connection between WAN blocking and these related technologies is crucial for organizations to make informed decisions about their network security strategies. By deploying and managing these technologies effectively, organizations can safeguard their WANs, protect sensitive data, and ensure the integrity and availability of their network resources.
Best Practices
Regular updates, monitoring, and testing are essential best practices for ensuring the effectiveness and reliability of WAN blocking. By implementing these practices, organizations can proactively identify and address potential security vulnerabilities, maintain optimal performance, and minimize the risk of successful cyberattacks.
Regular updates involve applying the latest security patches and updates to firewalls and routers used for WAN blocking. These updates often include fixes for known vulnerabilities and enhancements to security features, ensuring that WAN blocking remains effective against evolving cyber threats. Monitoring involves continuously observing and analyzing network traffic to detect any suspicious activities or attempts to bypass WAN blocking measures. By monitoring network logs and using intrusion detection systems, organizations can promptly identify and respond to potential security incidents.
Regular testing is crucial to validate the effectiveness of WAN blocking configurations and identify any weaknesses. Penetration testing or vulnerability assessments can be conducted to simulate real-world attacks and evaluate the robustness of WAN blocking measures. This allows organizations to proactively address any gaps in their security posture and make necessary adjustments to strengthen their defense mechanisms.
The practical significance of these best practices lies in their ability to enhance the overall security posture of an organization's WAN. By regularly updating, monitoring, and testing WAN blocking measures, organizations can proactively mitigate security risks, prevent unauthorized access, and protect sensitive data from cyber threats.
Future Trends
The future of WAN blocking lies in its integration with cloud-based security solutions. Cloud-based security solutions offer several advantages over traditional on-premises solutions, including increased scalability, flexibility, and cost-effectiveness.
One of the key benefits of cloud-based security solutions is their ability to provide real-time threat intelligence. Cloud-based security providers have access to a vast pool of data on cyber threats, which they can use to develop and deploy new security measures quickly. This allows organizations to stay ahead of the latest threats and protect their WANs from emerging.
Another benefit of cloud-based security solutions is their ability to provide centralized management and reporting. This makes it easier for organizations to manage their WAN blocking policies and track their effectiveness. Cloud-based security solutions also provide a single pane of glass for security monitoring, making it easier for organizations to identify and respond to security incidents.
The integration of WAN blocking with cloud-based security solutions is a key trend that will continue to shape the future of network security. By leveraging the benefits of cloud-based security, organizations can improve the security of their WANs and protect their data from cyber threats.
WAN Blocking FAQs
This section addresses frequently asked questions and misconceptions about WAN blocking, providing clear and informative answers to enhance understanding and implementation.
Question 1: What is WAN blocking?
WAN blocking refers to security measures implemented on Wide Area Networks (WANs) to prevent unauthorized access from the Internet. It involves using firewalls or routers to block incoming traffic from specific ports or IP addresses associated with known threats or suspicious activities.
Question 2: Why is WAN blocking important?
WAN blocking is crucial for safeguarding WANs from cyber threats such as malware, phishing attacks, and unauthorized access attempts. It protects sensitive data, ensures network integrity, and improves overall network performance by reducing unwanted traffic.
Question 3: How does WAN blocking work?
WAN blocking operates by configuring firewalls or routers to block traffic based on predefined rules. It examines incoming network packets and compares them against security policies. If a packet matches a blocking rule, it is discarded, preventing unauthorized access to the WAN.
Question 4: What are the benefits of WAN blocking?
WAN blocking provides numerous benefits, including protection from malware, phishing attacks, and other threats. It enhances network security, ensures compliance with data protection regulations, and improves network performance by reducing unwanted traffic.
Question 5: What are the technical considerations for WAN blocking?
WAN blocking requires careful configuration and maintenance. It involves updating firewalls and routers with the latest security patches, monitoring network traffic for suspicious activities, and regularly testing the effectiveness of blocking measures to ensure optimal protection.
Question 6: What are the future trends in WAN blocking?
The future of WAN blocking involves integration with cloud-based security solutions. Cloud-based security offers advantages such as real-time threat intelligence and centralized management, enhancing the effectiveness and scalability of WAN blocking measures.
In summary, WAN blocking is a critical security measure for protecting WANs from cyber threats and ensuring network integrity. By understanding the fundamentals, benefits, and best practices of WAN blocking, organizations can effectively implement and manage these measures to safeguard their networks and data.
For further insights and guidance on WAN blocking, refer to the main article sections that follow.
WAN Blocking Best Practices
To effectively implement and manage WAN blocking measures, consider the following best practices:
Tip 1: Regular Updates and Patching
Ensure that firewalls and routers used for WAN blocking are regularly updated with the latest security patches. This helps address known vulnerabilities and enhances the overall effectiveness of WAN blocking measures.
Tip 2: Continuous Monitoring
Monitor network traffic continuously to detect any suspicious activities or attempts to bypass WAN blocking measures. Utilize intrusion detection systems and analyze network logs to identify potential security incidents promptly.
Tip 3: Regular Testing and Validation
Conduct regular penetration testing or vulnerability assessments to validate the effectiveness of WAN blocking configurations and identify any weaknesses. This proactive approach allows organizations to address any gaps in their security posture.
Tip 4: Centralized Management
Consider using a centralized management platform for WAN blocking measures. This provides a single pane of glass for managing and monitoring security policies, simplifying administration and improving overall network security.
Tip 5: Integration with Cloud-Based Security Solutions
Explore the integration of WAN blocking with cloud-based security solutions. Cloud-based security offers real-time threat intelligence and centralized management, enhancing the effectiveness and scalability of WAN blocking measures.
Summary: By following these best practices, organizations can strengthen their WAN security posture, protect sensitive data, and minimize the risk of successful cyberattacks.
For a comprehensive understanding of WAN blocking, refer to the main article sections that follow.
Conclusion
WAN blocking plays a crucial role in safeguarding Wide Area Networks (WANs) from unauthorized access and cyber threats. Its importance lies in protecting sensitive data, maintaining network integrity, and improving overall network performance. By understanding the fundamentals of WAN blocking, its benefits, and best practices, organizations can effectively implement and manage these measures to protect their networks and data.
As the digital landscape continues to evolve, WAN blocking will remain a critical security measure for organizations of all sizes. Its integration with advanced technologies, such as cloud-based security solutions, will further enhance its effectiveness and scalability. By embracing WAN blocking and staying abreast of emerging trends, organizations can proactively protect their WANs and ensure the security and integrity of their networks.

Detail Author:
- Name : Prof. Ruthie O'Conner DVM
- Username : aleffler
- Email : juvenal.nicolas@schoen.info
- Birthdate : 1996-04-05
- Address : 54214 Stephany Shoals O'Connerchester, MT 89901
- Phone : (330) 958-1384
- Company : Feil Group
- Job : Urban Planner
- Bio : Enim et nostrum eaque consequatur. Dolorem dolore et minus nemo. Magni accusamus ab quaerat magni.
Socials
facebook:
- url : https://facebook.com/leannon1995
- username : leannon1995
- bio : Ullam culpa quia rerum earum voluptatibus enim quisquam.
- followers : 347
- following : 1725
tiktok:
- url : https://tiktok.com/@leannon2017
- username : leannon2017
- bio : Sint maiores numquam eos totam. Ut sed nobis nihil expedita quod ut.
- followers : 4646
- following : 589
linkedin:
- url : https://linkedin.com/in/kelly_dev
- username : kelly_dev
- bio : Corporis sit alias sed.
- followers : 6885
- following : 2995